This guide lets you configure Okta's SCIM provisioning feature to automatically grant RudderStack access to your users. It is divided into the following sections:
Supported features
Currently, RudderStack supports the following provisioning features:
- Push users: You can create or link a user in RudderStack when assigning the app to a user in Okta.
- Update user attributes: Okta updates a user's attributes in RudderStack when the app is assigned to them. Note that any future attribute changes made to the Okta user's profile will automatically overwrite the corresponding attribute value in RudderStack.
- Deactivate/reactivate users: This feature deactivates a user's RudderStack account when it is unassigned in Okta or their Okta account is deactivated. To reactivate the account, you can reassign the app to the user in Okta.
Requirements
To configure the SCIM app, you need a personal access token with admin privileges.
Follow these steps to create a new personal access token:
- Log in to the RudderStack workspace you want to enable SCIM for. Note that your role in the organization must of the Admin type.
- Go to Settings > Account tab and scroll down to Personal access tokens. Then, click Generate new token, as shown:
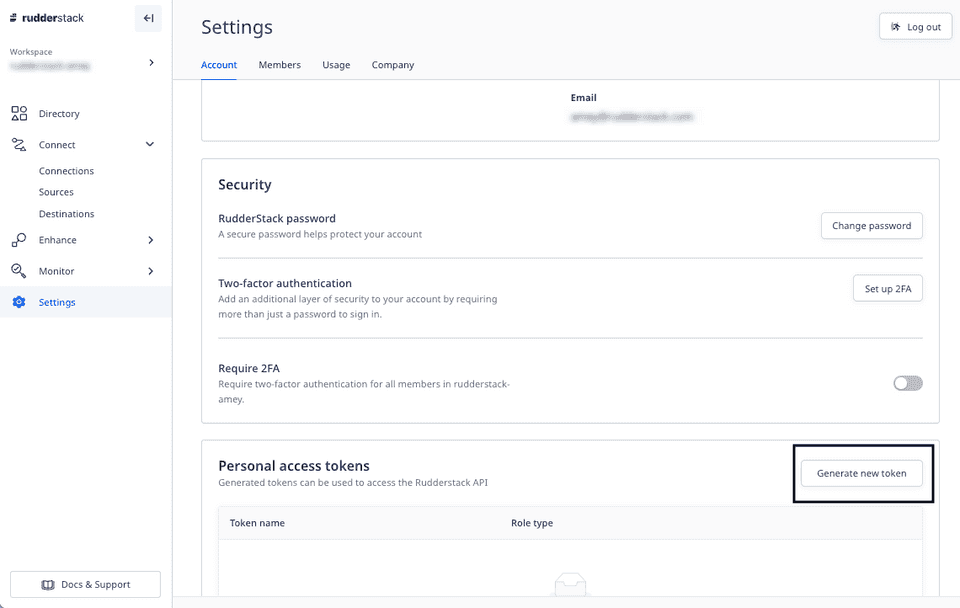
- Enter the token name and select Admin from the Role dropdown.
- Click Generate and save the token securely. It will not be visible again once you close this window.
Configuration steps
- Log in to Okta as an administrator.
- In the sidebar, go to Applications > Applications and select your SSO app.
- In the app settings, go to the Provisioning tab and and click Configure API Integration.
- Check the Enable API Integration setting.
- In the API Token field, enter the personal access token you generated above.
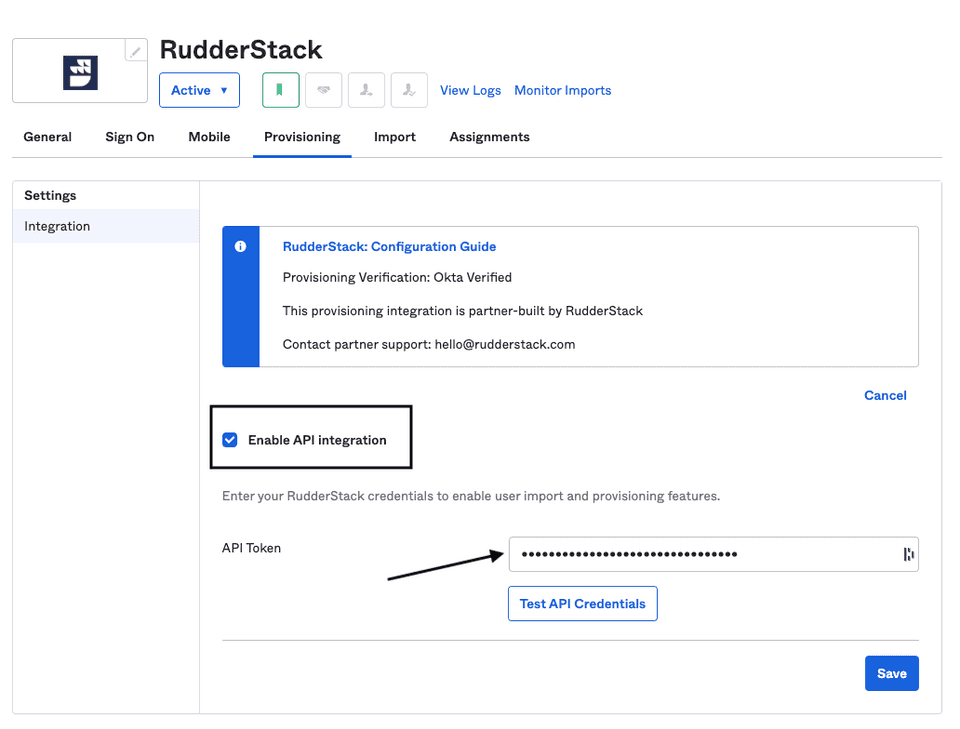
- Click Save to finish the configuration.
Known issues
Currently, RudderStack does not support the following SCIM features:
- Import users
- Import groups
- Push groups (will be supported in the future)
- Remove users
- Sync password
- Enhanced group push
Contact us
For more information on the topics covered on this page, email us or start a conversation in our Slack community.